As of ASA version 9.12 you may experience issues with some applications that use SSH. You may get an error that you’re unable to connect or login to the device, even though you’re certain that your username and password are correct. This happens with applications that use SSH (for example the config management of Solarwinds or Putty (prior to version 0.71)).
Cause
By default, ASA 9.12 and beyond, will use a new DH key exchange mode. This is dh-group14-sha256. Before this version, only DH group 1 with SHA1 was supported. SHA256 is not activated by default in most applications or they simply do not support them.
Solution
You can solve this by either making sure your application can use SHA256 with Diffie Hellman group 14, or by altering the key exchange group in the ASA.
As we are no application managers, we will not describe how you can alter your application. For that, you can find a variety of websites describing the way to alter the hashing algorithms and key exchanges online. If you have issues with Putty, we highly recommend upgrading to the latest version. Putty supports SHA256 as of version 0.71.
For ASA you can use either the CLI or the ASDM gui to alter your key exchange group.
These are the CLI commands you can use for altering the key-exchange group:
ASAv1# configure t
ASAv1(config)# ssh key-exchange group ?
configure mode commands/options:
dh-group1-sha1 Diffie-Hellman group 2
dh-group14-sha1 Diffie-Hellman group-14-sha1
dh-group14-sha256 Diffie-Hellman group-14-sha256
ASAv1(config)# ssh key-exchange group dh-group14-sha1
ASAv1(config)#
For ASDM, you need to navigate to Device management > Management access > ASDM/HTTPS/Telnet/SSH. On the bottom part of the page you can find the DH Key Exchange.
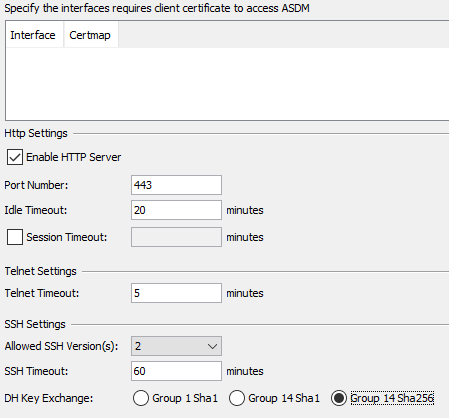
Just click the key exchange you want to and apply the configuration.
